Illustrated instruction of setting the SPF and DMARC records
1. Login with your credentials of your customer account on admin.forpsi.com.
2. Click on the "Domains" link
3. Click on the domain name

4. Click on the "edit DNS records" link (if this button is missing, you don't use our NS servers and you have to set these TXT records on your NS servers)
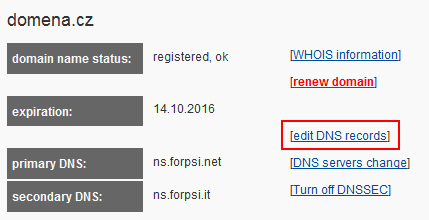
5. The SPF record is a TXT record of the domain. We recommend the value
v=spf1 a mx include:_spf.forpsi.com -all
At first, check if the SPF record of the domain is set. The domain can have only one SPF record
If the SPF record has the policy Softfal (~all) or Neutral (~all), we recommend from safety reason to change it to Fail (-all). After clicking on the Edit button, you can change the value in the fields on the bottom (the sam fields as for adding the new records. Edit the value and svae changes.
5. Add the DMARC record as a TXT record with the hostname _dmarc, we recommend the value with reject policy v=DMARC1; p=reject. If you have set the DMARC with the policy none, or quarantine, we recommend to change it to reject (prevent to deliver fraudulent emails with forged domain in the From parameter in headers
SPF records of external services If you send emails through the smtp server of your ISP, from internal system, or you are using some marketing services, it is neccessary to allow also IPs of these services. Because every domain can have set only one SPF record, you have to add items of external services into the existing SPF record. It can be
An IP address "ip4:XXX.XXX.XXX.XXX", resp. ip6, or a range of IP addresses "ip4:XXX.XXX.XXX.XXX/24", resp. ip6.
An item of external service, see samples bellow
- Office365: include:spf.protection.outlook.com
- Shoptet: include:_spf.myshoptet.com
- Mailchimp: "include:servers.mcsv.net"
- Google: include:_spf.google.com
Add the items into your SPF record, see sample
v=spf1 a mx include:_spf.forpsi.com include:spf.protection.outlook.com ~all
Qualifiers - determine proccessing your emails The mechanism and qualifiers all allow you to determine, how the emails, that do not correspond with allowed IP address, will be processed.
"-" Fail - the emails from disallowed IPs should be rejected.
"~" Softfail - typically, messages that return a Softfail are accepted but tagged.
In the sample "v=spf1 a mx include:_spf.forpsi.com -all", the qualifier Fail is used. Emails sent via our mailservers match the SPF test. Emails sent via other mailservers (e.g. SMTP server of the ISP) don't match the SPF test, and will be rejected. Choose this qualifier, if you exactly know, which servers you use to send your emails and if you want to secure your domain against abusing in spams.
If you choose the qulifier Softfail (~all), sample "v=spf1 a mx include:_spf.forpsi.com ~all", not matched emails will be accepted, but almost marked as spam.
The flow chart of DMARC check (combines DKIM and SPF)
Note
If the owner of the domain wants to set also the SPF2.0 record (SID), add into it the item
include:_sid.forpsi.com
The value of the SID record can be
spf2.0/pra a mx include:_sid.forpsi.com -all